Drones are being weaponized to intercept, inject & exploit mobile devices.
Drones on the battlefield are being used to compromise the phones and communications of troops on the ground, exposing intel and positions for immediate action.
The methods of interception and malware delivery are evolving.
- Fake base-stations (ISMI-catchers) perform MITM: intercept calls, SMS, data, and steal OTPs/credentials.
- Force protocol downgrades, jam networks, or induce fallbacks to insecure links to enable further espionage.
- Deliver/attach "sticky" spy payloads or push malicious SMS/links to implant malware and exfiltrate data.
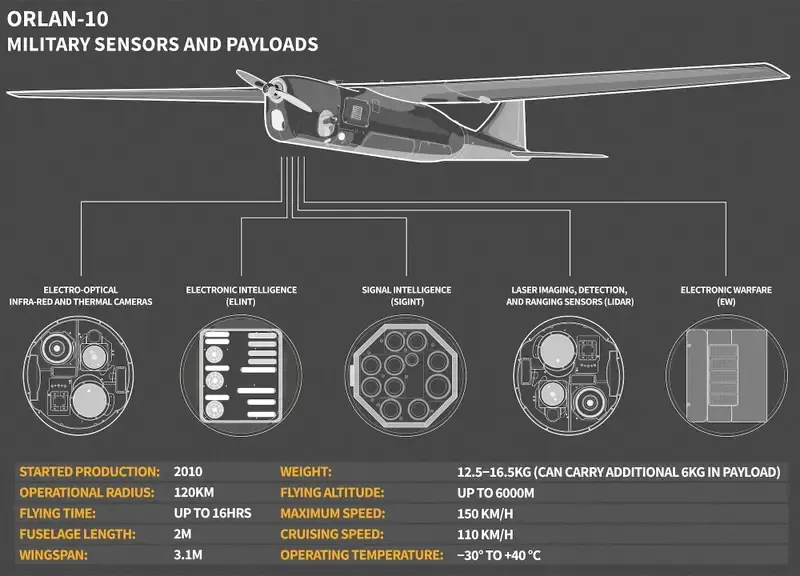
Electronic warfare packages can be easily equipped to serveral types of drones, allowing for adversaries to deliver remote malware and compromise communications in a variety of situations.

Depending on the attack method, drones can forward communications or enable remote exfiltration for immediate use by adversarial operators. Enabling rapid exploitation or targeting before defenders can detect and respond.
How Renati and ChatMail Strengthen Field Communications
A security-hardened Android platform that eliminates many of the traditional telephony and SMS attack surfaces exploited by adversaries. Incorporating built-in tamper detection to safeguard devices in the field with automatic self destruction if the device feels threatened.
Secure communications that leverage Post-Quantum Encryption (PQC) to prevent "harvest-now, decrypt-later" attacks, ensuring messages and calls remain cryptographically protected even if wireless links are intercepted.
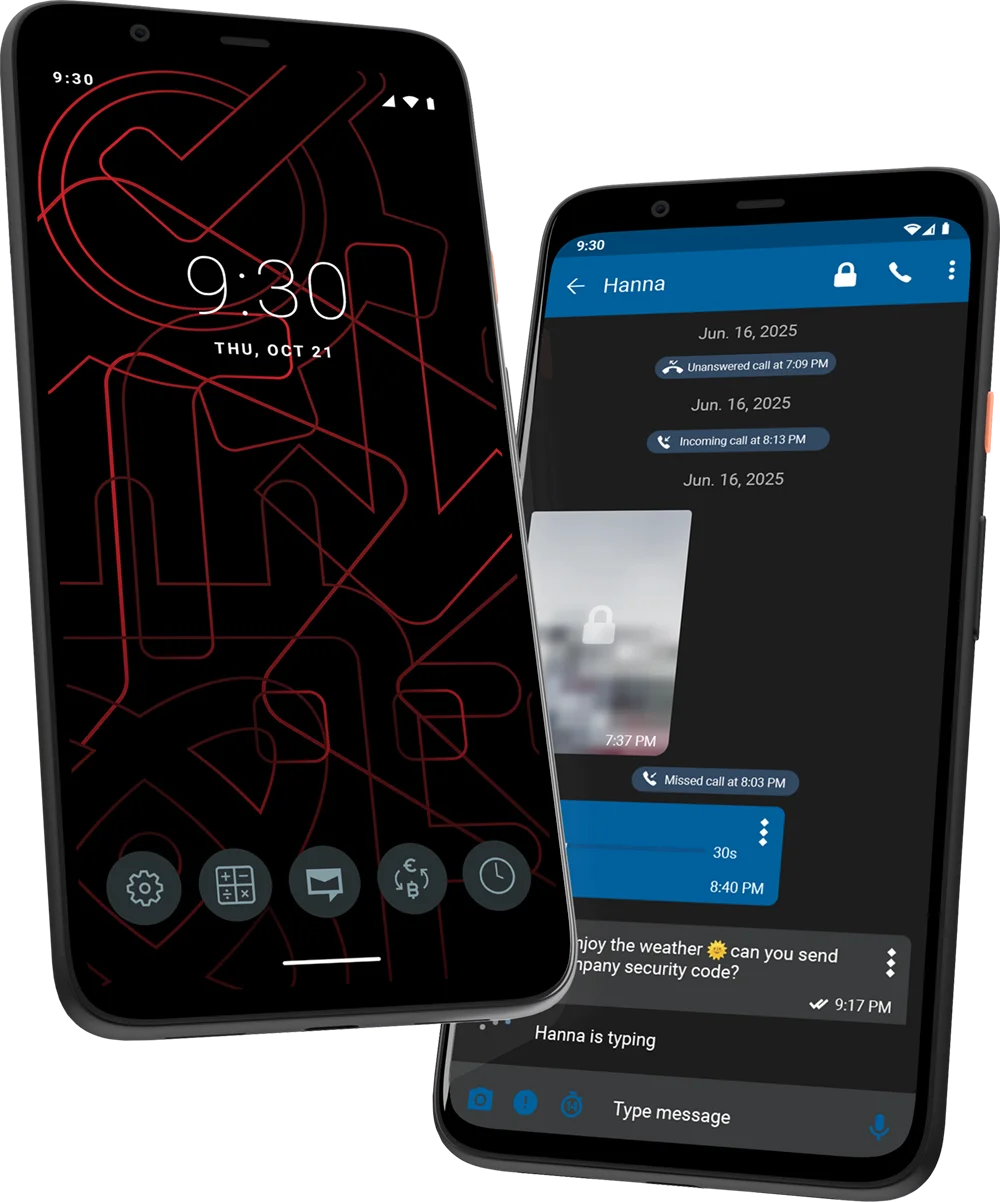

An integrated system provides instant provisioning, monitoring, application deployment and rapid revocation. Compromised or suspicious devices can be remotely disabled or wiped within seconds.

Customize your solution for independent secure communications.
Our solution excels in covert and clandestine operations where overt communications are not an option. When paired with our Mobile Communication Unit (MCU), field devices can be deployed and operational within minutes, requiring no technical training or external assistance.
